Symmetric Key Cryptography
Cryptography is very, very complex… As it should be. It keeps us and our data safe and secure.
This write-up will provide an overview of Symmetric Key Cryptography
Cryptography - What’s The Point?
There are many use cases for cryptography, but the most obvious is confidentiality. We want to ensure our private data remains private. Simple as that.
Cryptography can also be used to ensure integrity, Nonrepudiation, and authentication
Symmetric Key Cryptography
Symmetric key cryptography - the concept of using a single shared key to encrypt and decrypt data.
Both Bob and Alice must know the password (the key) to see what the other has written. This can be summed up with the image below:
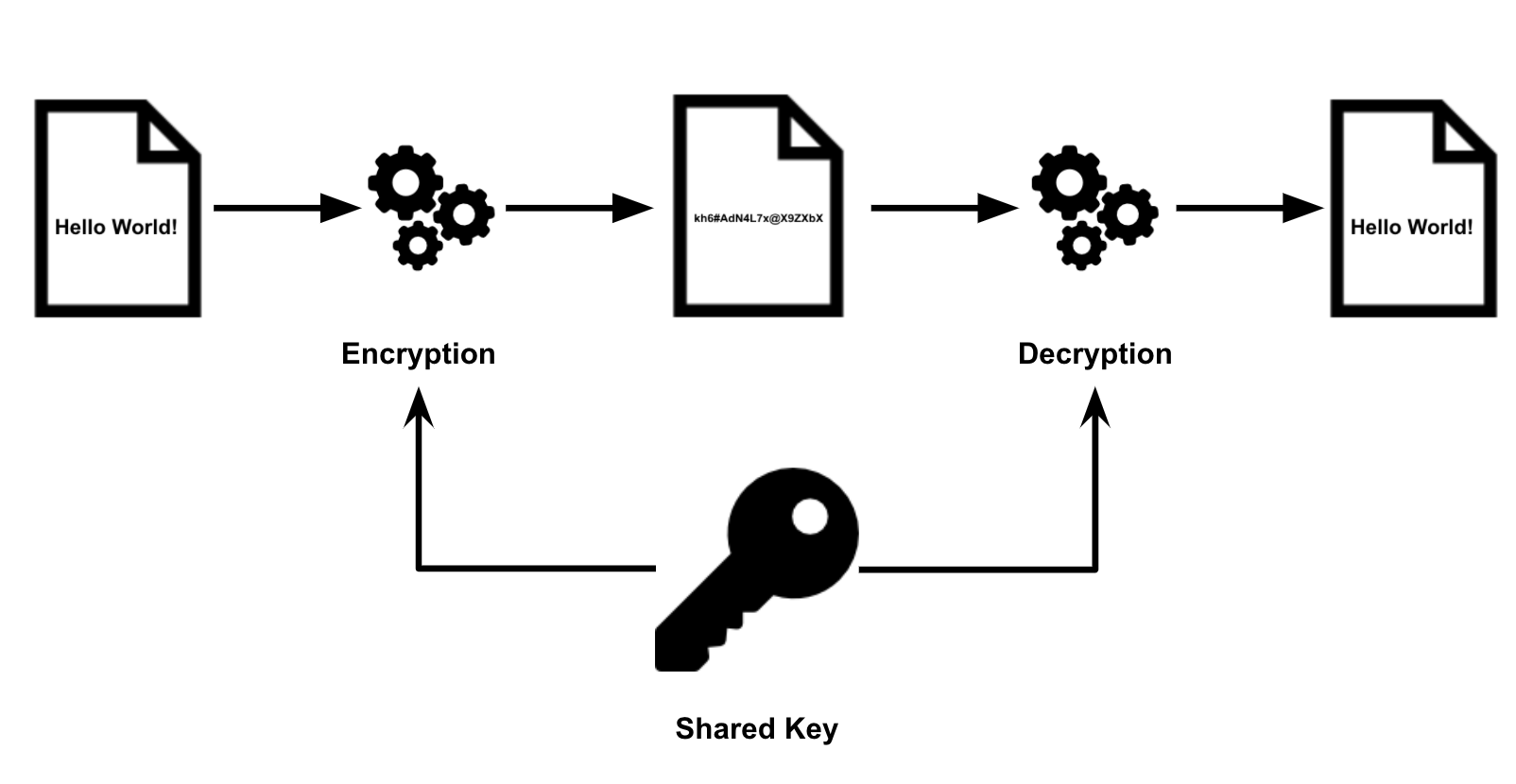
Strengths of Symmetric Key Cryptography
Symmetric key cryptography algorithms operate much, much faster than non-symmetric key cryptography algorithms.
Weaknesses of Symmetric Key Cryptography
Key Distribution… Sharing the key over a nonsecure connection exposes the password! No Nonrepudiation… We can not prove or confirm the person who sent us the message is who they say they are. Not Scalable… Someone must send us the key to use the key. Key Turnover… Everyone who uses our key knows our key. If one person leaves a brand new key must be created and distributed all over again.
Symmetric Key Ciphers
Data Encryption Standard (DES)
DES is a 64-bit block cipher and uses a 56-bit long key. DES performs 16 rounds of encryption, meaning the encryption/decryption operation is repeated 16 times. DES is no longer considered a secure symmetric key algorithm and should not be used. There are 5 different modes we can use with DES:
Electronic Code Book (ECB) - Least Secure
- ECB is the simplest and least secure mode we can use.
- There is no ‘randomness’ … Identical plaintext blocks create identical ciphertext blocks. This creates patterns. In cryptography patterns are BAD!
Cipher Block Chaining (CBC)
- CBC uses chaining, Each unencrypted block is XOR with the ciphertext of the previous block.
- The first block is XOR with an initialization vector.
- Errors from one block ‘travel’ to all of the following blocks… in other word, error’s propagate. This Destroys integrity.
Cipher Feedback Mode (CFB)
- CFB operates very similarly to CBC … it uses chaining and an initialization vector.
- CFB differs from CBC in that it operates against data in real time. Because of this , error’s do not propagate.
Output Feedback Mode (OFB)
- OFB operates very similarly to CFB and CBC … it uses chaining and an initializtion vector.
- Instead of XOR with the ciphertext of the previous block, OFB XOR with a seed value.
- Error’s do not propagate.
Counter Mode (CTR) - Most Secure
- Shares all OFB advantages, however CTR uses a simple counter for each operation. This allows us to perform encryption in parallel .
Triple DES
As computers became stronger and faster the original 56-bit key that DES used was easily brute forced. Triple DES was introduced to make DES encryption stronger. Triple DES uses the DES algorithm 3 times leading us to use 3 56-bit keys which ultimately gives us a168-bit key. The larger the key, the harder to brute force. Even though Triple DES has a 168-bit key it is only as strong as a 112-bit key. This is due to a meet-in-the-middle attack which Triple DES is vulnerable.
Advanced Encryption Standard (AES)
AES is the gold standard for Symmetric key cryptography today. AES allows the use of 128-bit, 192-bit, and 256-bit key lengths. AES is a block cipher and operates on 128-bit blocks. 128-bit keys require 10 rounds of encryption 192-bit keys require 12 rounds of encryption 256-bit keys require 14 round of encryption
Other Symmetric Key Block Ciphers
Cast-128 SAFER Blowfish Twofish RC5
RC4
RC4 is a symmetric key stream cipher. RC4 is the most commonly implemented symmetric key stream cipher